General Security Information
This section is intended to help you assess all aspects of data security and in particular to assess any compliance you may need to meet your country’s data protection requirements. For our customers in the EU, we have an additional guide to EU data protection available here.
How does Capsule ensure safe storage of the data I hold?
Our Technical Security page explains our approach to ensuring the safety of your data, including details on data center security, data encryption, location, security updates and third party reviews.
Who can access my Data?
You choose who to invite to your Capsule account and the permissions they have. You may also choose to grant access to other applications that integrate with Capsule. You should apply the same security assessment to any application or third party which you grant access to.
When you invite a user to Capsule, they choose a username and password that they will use to log-in to Capsule. Currently when a user sets a password, Capsule follows NIST guidelines which means the User must choose a secure password of at least 8 characters and that is not a commonly used password (such as password or 12345678). We may revise password rules inline with NIST or other best practice guidelines in the future.
Users should also enable Two-Factor Authentication (2FA) which helps protect a user’s account even if someone has obtained or guessed their password.
In the Users list of your Capsule account settings, you can see which users have enabled two-factor authentication.
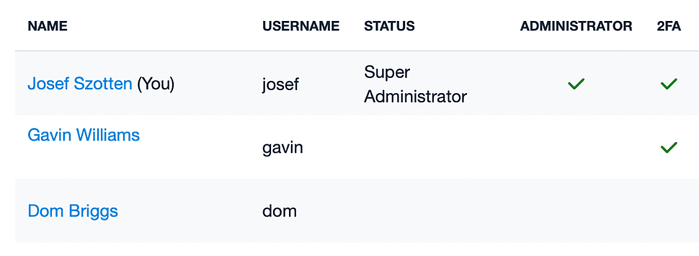
Your users are introduced to these requirements in the User Getting Started guide
What are Capsule’s service levels and can I access my data where and when I want it?
We aim to make Capsule available 24/7 and you can securely login to access your data at a time and place convenient to you through a PC, Mac, or your mobile phone.
Capsule benefits from Amazon’s EC2 Service Level Agreement which is designed to provide 99.95% uptime. Typically we achieve better than this and our published uptime report demonstrates our track record.
Capsule operates with spare capacity to support the demands of all customers, and because Capsule is hosted on a cloud platform, we can increase capacity at short notice. Fair use rate limits and other protections are also applied to all customers of Capsule to protect against one customer impacting the quality of the service.
Capsule staff and your data security
Your data is your data and we never touch your data without your explicit permission.
In order to provide the service, we do have authorized operations staff with access to the underlying infrastructure and therefore the underlying data in raw form. However we never access specific customer data unless we are working with the customer to investigate a problem and we have explicit permission from you to run a specific query on the data to help us narrow down the issue.
Our team security:
- Each person in our team is contracted with the highest level of confidentiality
- Capsule staff (or 3rd parties we use) do not have access to passwords or the ability to login to your account. You may choose to invite us as a temporary user to help us to solve a question you have.
- We never have access to full payment card information all of which are stored outside of our servers
Will my data be shared with third parties?
We will never disclose your personal information to anyone else except where we have to do so in accordance with our Privacy Policy, especially the section called ‘Disclosure of your Information’
What information is available to monitor who is accessing my data?
Your Super Administrator(s) can monitor log-in activity on the account by visiting:
- Go to the Account SettingsUsers & Teams
- Go to the Recent Logins tab.
Capsule Certification
We comply with EU General Data Protection Requirements (GDPR). The Data Commission Offices in the EU don’t require or offer a certificate we could apply for. Their requirements are that we meet the legislation, of which we are already compliant.
This article is particularly helpful in explaining. There are no bodies that have been empowered by the EU Commission Offices to audit and certify GDPR compliance. All that said, we can assure you Capsule offers the security required for you to be compliant, e.g. encryption and legal agreements, and Capsule has the functionality for ensuring you can act responsibly with your customer’s data.
We have been asked about ISO and SOC certification. These are not directly linked to or related to the GDPR. These are certifications that confirm security levels, ISO primarily in the EU and SOC primarily in the US. We have achieved our SOC 2 Type II accreditation which you can read about further in this article.
How is my data encrypted?
Data that is transferred between you and Capsule is encrypted in transit using transport layer security (TLS). We work hard to support the highest possible cryptographic standards for encryption of data in transit and we disable support for any older standards that are no longer considered strong. All customer data is encrypted at rest.
What happens when I cancel my account?
As described in the Termination & Cancellation section of the Capsule Terms:
“When an account is terminated or cancelled, the account and any content left behind in the account will be made inaccessible. For a period of 14 days after any account has been cancelled you may request that we restore your account. After this period, your account and all Customer Data contained within it will be permanently deleted and the agreement between us as set out in these Customer Terms will automatically terminate. Please be aware that partial data may reside in our backup and/or archive systems for a period of up to 50 days.”
How do I backup my data?
Capsule provides a function to export your data to a ZIP file. The ZIP file in turn contains a separate CSV file for your Contacts, Projects and Opportunities with all their details including notes & email history. The CSV files can be opened in a range of spreadsheet applications. An Administrator can export a backup like this:
- Navigate to the Account Settings, then select Export Data.
- Click the button to Export to ZIP file.
- An email will be sent to the first email address on your user record containing the ZIP file with the data in it.
You can read more about how to export your account for backup in our export article.
How is my data protected from accidental destruction?
Our systems automatically replicate your data across multiple locations in real-time to maximize availability. Data is also constantly backed up to ensure we can restore access to your data and the service in the unlikely event that the data replicas in all locations fail at once.
In the event that one of your users accidentally deletes a record, the Super Administrator has 30 days to restore it. Read more on how to restore records
In addition, you have the ability and are encouraged to download and retain your own backup
In the event of data breach, what is Capsule’s notification and alert process?
Amazon are responsible to make sure their data centers and the services they provide are secure and to notify us of a breach. Amazon take both physical and network security seriously, ensuring your data is safe: http://aws.amazon.com/security/. We provide security above these services provided by the infrastructure.
For breaches our preferred approach is to limit the possibility of them happening in the first instance. We have robust internal processes to ensure prompt installation of security updates, protection of our assets (including two-factor authentication to sensitive systems), and also to limit access to data to key staff on a needs-only basis. Additionally, no one in our company has the right to access your data without your permission. We also engage a third-party penetration testing organisation to validate our security and review our application code.
In the event that a security breach was detected we would perform an investigation to understand the scope of the breach and if any data was affected. Depending on the nature of the breach we would make our best efforts to understand what has happened as soon as possible. We would aim to inform you as soon as possible and not later than 72 hours if you have been affected by the breach.
While we are able to secure our servers you as the data controller for your account have a responsibility to ensure your team also follows good security practice. For example, making sure that each service they use has a strong, unique password and consider enabling two-factor authentication.
Data Protection and the EU GDPR Legislation
Capsule has used the EU’s General Data Protection Regulations (GDPR) to set the standard for Data Protection. It applies to anyone storing Personal Data about any EU resident. We encourage all customers to assess their data protection compliance, whether in the EU or elsewhere in the world, on the basis of how we meet these standards. In addition to this article, we’ve prepared a GDPR FAQ to help you complete a risk analysis for yourself or your organization.
Data Location
All Capsule data is stored with Amazon Web Services (AWS) in the United States. Any data stored outside of the EU has to be in a safe country or with a company that complies with the safeguards required by the GDPR legislation.
We have agreed a Data Processing Addendum with AWS that commits them to the Model Contract Clauses, defined by the European Commission. This ensures safe transfer of data to AWS in accordance with EU data protection laws.
Further information on Model Contract Clauses can be found in the UK Information Commissioner’s Office (ICO) guide
Obligation and contractual requirements of you as Data Controller
The responsibility for complying with the Regulations rests with the Data Controller. As you are the Data Controller in respect of personal data you store on Capsule, it is your responsibility to ensure compliance with this law if you are storing EU customer data.
In order to make an assessment of whether Capsule allows you to meet the requirements, we recommend that you carry out a simple risk analysis. Answers to these common GDPR questions will help you complete a risk analysis for yourself or your Organization. We do so with the firm belief that Capsule is well placed to protect the personal data that you entrust to us.
Obligation and contractual relationship as your data processor
Capsule has a legal obligation to protect your customer’s Personally Identifiable Information. Please read through the Data Processing Agreement to understand our commitments and approach to protecting the data you store on your account.
Obligations and contractual relationships with our sub-processors
Capsule has a number of sub-processors, for example, AWS. All of these sub-processors have agreements in place to ensure your customer data is protected as if we were taking care of it directly in the EU. A list of our sub-processors is maintained here.
Capsule Features Which Support Your Compliance Requirements
Recording consent
The GDPR requires all EU customer data to have a lawful basis for processing. Consent is one of the ways to ensure lawful processing. Others include your right to process a customer’s data because of legitimate interest. The UK Information Commissioner’s Office (ICO) has published draft guidance notes on the lawful basis for processing that will be helpful in learning more about what it entails and whether you need to seek pro-active consent. Click here for that guidance.
If you do need to record a customer’s pro-active consent, you can use Capsule’s Custom Fields feature, and add a checkbox field to record that consent has been given. This can be teamed with a date field to record when consent was given.
Another possible way of highlighting customers who have consented to you processing their data is by using a DataTag. DataTags allow you to capture additional information with a tag. For example, you might like to create a ‘Consent’ tag and record the date consent was given alongside the tag.
Right to be Forgotten
Under the GDPR there is an emphasis on the right to be forgotten, enabling an individual to request that their data be deleted. If one of your customers asks you to delete their information you can use the Capsule ‘Trash Can’ function to do this.
A deleted Contact remains in the trash can for 30 days after which the data is permanently removed from our live database. There is also an option that allows Super Administrators to purge individual contact records from the account immediately, overriding the 30 days in the trash can.
Capsule does retain backups. As explained in our Customer Terms, we ensure any residual data is cleared within 50 days of the data being removed from the live systems. You can read about the current deletion and retention policy that is in place here.
Subject Access Request (SAR)
Subject Access Requests are something that has been a requirement under previous legislation but has become more prominent with the introduction of the GDPR. With this, an individual may request access to all of the data you have stored about them in Capsule.
When requested, a SAR can be prepared by an Administrator Capsule user with export rights using the 'Print Summary' feature. This will contain customer details completed with all history and notes. To do this:
- Open up the Contact who has requested their data
- Next to the Contact name, use the downward arrow to open up an actions menu
- Select Print Summary
- Print the Page
- You can now use the print function in your browser to print the information, or generate a PDF for example
How Capsule processes your data
We will only process your personal data according to your instructions as Data Controller in accordance with our Terms and Privacy Policy.